By Kevin J. Collins, RPLU, Associate AIA

Architects encounter cyber risks every day, often without considering the implications of the risks they face. Building awareness and creating greater understanding of the common cyber risks will help architects manage their exposure to hackers and other bad actors.
Understanding cyber threats: The broad brush
Many of the notable data breaches that occurred over the last few years were the result of attacks that exposed credit card data and volumes of personally identifiable information. These breaches potentially compromised the safety of the affected organizations and endangered the security of millions of individuals who were exposed to the possibility of identity theft.
As an architect, if you don't think you need cyber protection or don't believe someone would want to hack into your system, you may already be in trouble. It’s tempting to think that your practice is small or not well known, or if you’re not in one of the most frequently attacked industries, you may not have much to worry about. Unfortunately, that is not the way hackers are thinking. Companies of all sizes and in all industries are at risk, including architects.
Different types of cyberattacks:
- Security event: an event on a system or network detected by a security device or application.
- Security attack: a security event that has been identified by correlation and analytic tools as malicious, activity that is attempting to collect, disrupt, deny, degrade or destroy information system resources or the information itself.
- Security incident: an attack or security event that has been reviewed by an analyst and deemed worthy of further investigation.
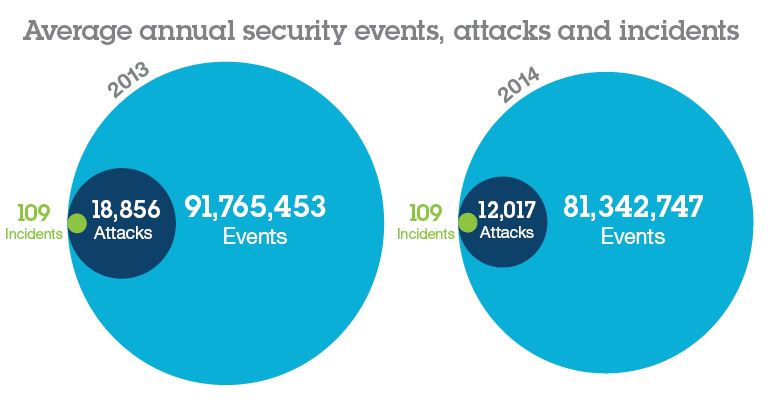
Recent trends: How the cyber risk is evolving
Over the past few years, malicious code and sustained probes and scans accounted for most of the security incidents. However, all that changed in 2014 when certain types of unauthorized access incidents rocketed to the top, accounting for 37 percent of the total. However, with an ever-expanding array of malware for which attackers may choose—including viruses, worms, Trojans, spyware and adware—it seems certain that malicious code incidents will continue to wreak havoc for the foreseeable future. Attackers are typically interested in finding the path of least resistance and these methods can provide that.
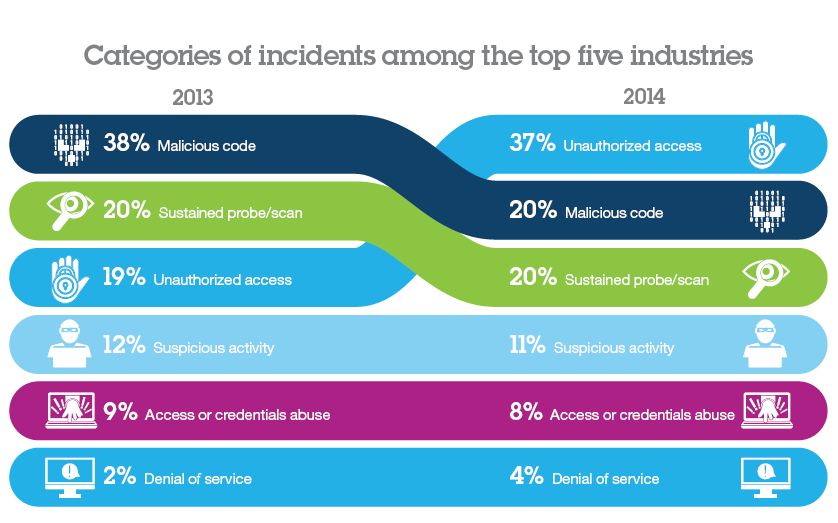 attribution to IBM Security Intelligence 2015
attribution to IBM Security Intelligence 2015
Everyday cyber risks of architects: Recognition is the first step to mitigation
Business Interruption: AAA Architects, Inc. launched a new website allowing users to access their projects, schedule meetings and appointments, and monitor the architects progress. One month after the website launched, the website was compromised by a distributed denial of service (DDoS) attack by a hacker. It took nearly a week for AAA Architects staff to bring the website back online. They had been the victim of a DDoS attack that disabled the company’s network and online services.
Cyber Extortion: Smith & Smith, LLC, a mid-sized architecture firm, held confidential information on many of their clients. A hacker based in Russia gained access to their computer system and sent an email with a copy of a project file from one of the firm’s clients. The hacker threatened that unless they are wired $250,000 they would not only shut down the firm’s computer systems, they would also publish all the data obtained from the system.
Digital Asset Loss: XYZ Architecture just put the finishing touches on a set of 3D CAD drawings for a new academic building at a local university. The firm sent out an internal communication thanking everyone for their hard work on the project and announcing that the job was nearly ready to deliver to the project owner. Later that night, a disgruntled IT administrator accessed and destroyed the CAD files, destroying months’ worth of hard work and putting the firm in danger of losing its contract with the university.
Telephone Toll Fraud: ABC Architects, LLP installed a VoIP telephone system in their new office location. The firm had several international projects and the VoIP system offered by their local telephone carrier had attractive rates on international calls. Two months after opening the new location, ABC Architects received a telephone bill totaling $175,000. Upon investigating the phone bill, they discovered hundreds of calls placed on the last Saturday of the previous month. They determined that they were a victim of telephone toll fraud. Hackers had breached their VoIP system and routed hundreds of phone calls through a premium 900 number. The phone carrier claimed ABC Architects did not have strong internal controls in place and refused to let them out of the bill.
For each of these instances, there is a preventative measure that would have well served the architectural firms that were victimized.
A call to action
Architects must educate their employees, clients, and vendors to these risks and take the appropriate actions to protect their information. Follow these security essentials to create a more secure environment for your business:
- Build a risk-aware culture - Whether you open a dubious attachment, use an infected flash drive, or fail to install a security patch on your laptop, everyone is at risk. Educate your employees about cyber risks and the measure they can take to protects themselves and the company.
- Manage and report all incidents - Report all cyber-attacks and potential attacks to local authorities or insurance carrier. Security breaches that occur at different companies or different locations may be related, but this can only be discovered if incidents are reported and analyzed.
- Defend the workplace - Ensure all devices connected to a network - from a laptop to a printer to a smart TV - are up to date with the latest security software and follow all cyber security management and policy enforcement. Ensure frequent, regular system back-ups are performed.
- Security by design - One of the biggest vulnerabilities in information systems - and wastes of money - comes from implementing services first and add security on as an afterthought. Build security into your network from the beginning and maintain regular tests to track conformance and compliance.
- Keep it clean - Cyber criminals target people and businesses that are using old, out of date software. Maintain a comprehensive security system and install necessary updates and patches as they are released.
- Control network access - Companies that channel registered data through monitored access points will have a far easier time spotting and isolating malware.
- Security in the clouds - If your company utilizes public cloud data centers, ensure you have the tools and procedures in place to monitor possible threats and isolate your data from other companies in that data center.
- Patrol the neighborhood - Ensure your vendors and clients are also aware of your risk-aware culture.
- Protect the company's crown jewels - Every company has crown jewels, whether it is scientific data, acquisitions documents, or clients financial and person information. Whenever your company carries out an inventory, critical data should get special treatment, guarded, tracked and encrypted as if the company's survival depends on it.
- Track who's who - Ensure you have procedures in place to manage the access and permissions of your employees. When an employee leaves, you must have the control to revoke immediately any access they have to company, client, and vendor information.
Conclusion
Although dealing with risks such as professional liability, client expectations, and solving difficult design issues are often easier to address, more interesting, or may be more top-of-the-mind for every architectural firm, understanding that you are a business and are not immune to the risks of technology and cyber-crime is a vital first step to addressing these risks proactively. Implement the 10 steps listed above. Consider cyber liability insurance to protect your firm—and find out more about it in The Architect’s Guide to Buying Cyber Liability Coverage—to help transfer your cyber risks, evaluate the cyber liability policy options available to you, and select the best match in terms of limits and coverage to meet your needs.
_____________________________________
Kevin Collins, RPLU, Associate AIA, is a Senior Vice President with Victor O. Schinnerer & Company, with more than 20 years’ experience working with design firms and other construction-related professional service firms on issues of professional liability exposure and business risks. He has spoken extensively on challenges to the design profession and a wide array of practice management issues. For more information you can reach the author at Kevin.J.Collins@Schinnerer.com or 301-951-5412.
(Return to the cover of the 2018 PM Digest: Tech Trends)